- Road No - 3, Banjara Hills, Hyderabad.
- +91-94919 42943
New Akira Ransomware
New Akira Ransomware Operation Hits Corporate Networks
A new ransomware operation called Akira has been slowly building a list of victims over the past few months by breaching corporate networks worldwide, encrypting files, and demanding million-dollar ransoms. Since its launch in March 2023, Akira claims to have already conducted attacks on sixteen companies across various industries, including education, finance, real estate, manufacturing, and consulting. While another ransomware named Akira was released in 2017, it is not believed that these operations are related.
The Akira encryptor
A sample of the Akira ransomware was discovered by the MalwareHunterTeam, who shared it with BleepingComputer for analysis. When executed, the ransomware first deletes Windows Shadow Volume Copies on the device by running a PowerShell command:
powershell.exe -Command “Get-WmiObject Win32_Shadowcopy | Remove-WmiObject”
Then, the ransomware will initiate encryption of files with specific extensions listed below:
.accdb, .accde, .accdc, .accdt, .accdr, .adb, .accft, .adf, .ade, .arc, .adp, .alf, .ora, .btr, .ask, .cat, .bdf, .ckp, .cdb, .cpd, .cma, .dad, .dacpac, .daschema, .dadiagrams, .db-shm, .db-wal, .dbf, .dbc, .dbt, .dbs, .dbx, .dbv, .dct, .dcb, .ddl, .dcx, .dlis, .dsk, .dqy, .dtsx, .dsn, .eco, .dxl, .edb, .ecx, .exb, .epim, .fdb, .fcd, .fmp, .fic, .fmpsl, .fmp12, .fol, .fpt, .gdb, .frm, .gwi, .grdb, .his, .hdb, .idb, .itdb, .ihx, .jet, .itw, .kdb, .jtx, .kexic, .kexi, .lgc, .kexis, .maf, .lwx, .mar, .maq, .mav, .mas, .mdf, .mdb, .mrg, .mpd, .mwb, .mud, .ndf, .myd, .nrmlib, .nnt, .nsf, .nyf, .nwdb, .oqy, .odb, .owc, .orx, .pdb, .pan, .pnz, .pdm, .qvd, .qry, .rctd, .rbf, .rodx, .rod, .rsd, .rpd, .sbf, .sas7bdat, .sdb, .scx, .sdf, .sdc, .spq, .sis, .sqlite, .sql, .sqlitedb, .sqlite3, .temx, .tps, .tmd, .trm, .trc, .udl, .udb, .usr, .vpd, .vis, .wdb, .vvv, .wrk, .wmdb, .xld, .xdb, .abcddb, .xmlff, .abx, .abs, .adn, .accdw, .icg, .hjt, .kdb, .icr, .maw, .lut, .mdt, .mdn, .vhd, .vdi, .pvm, .vmdk, .vmsn, .vmem, .nvram, .vmsd, .raw, .vmx, .subvol, .qcow2, .vsv, .bin, .vmrs, .avhd, .avdx, .vhdx, .iso, .vmcx
, skipping files found in the Recycle Bin, System Volume Information, Boot, ProgramData, and Windows folders, as well as Windows system files with .exe, .lnk, .dll, .msi, and .sys file extensions. When encrypting files, the ransomware appends the .akira extension to the file’s name.
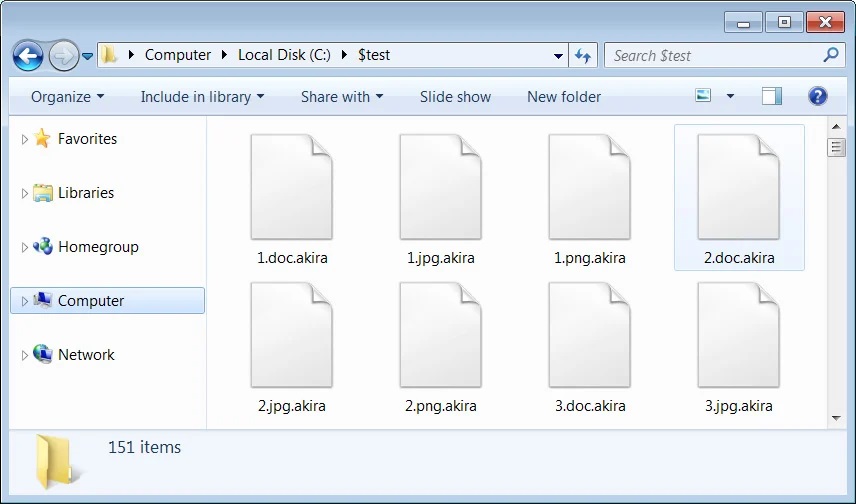
Files encrypted by Akira
Source: BleepingComputer
Akira uses Windows Restart Manager API for more effective encryption
One unique aspect of Akira is its use of the Windows Restart Manager API to close processes or shut down Windows services that may be keeping a file open and preventing encryption. This allows the ransomware to more effectively encrypt files and maximize its impact.
Each victim of Akira has a unique negotiation password that is entered into the threat actor’s Tor site, which features a chat system that the victim can use to negotiate with the attackers. However, unlike many other ransomware operations, Akira’s negotiation site does not include a payment portal, and all negotiations are conducted through the chat system.
Akira’s ransom note is named akira_readme.txt and is included in each encrypted folder. It includes information on what happened to the victim’s files and links to the Akira data leak site and negotiation site. The note warns that if negotiations fail, the attackers will try to sell personal information, trade secrets, databases, and source codes on the dark market to multiple threat actors at once, and all of this will be published on the attackers’ blog.
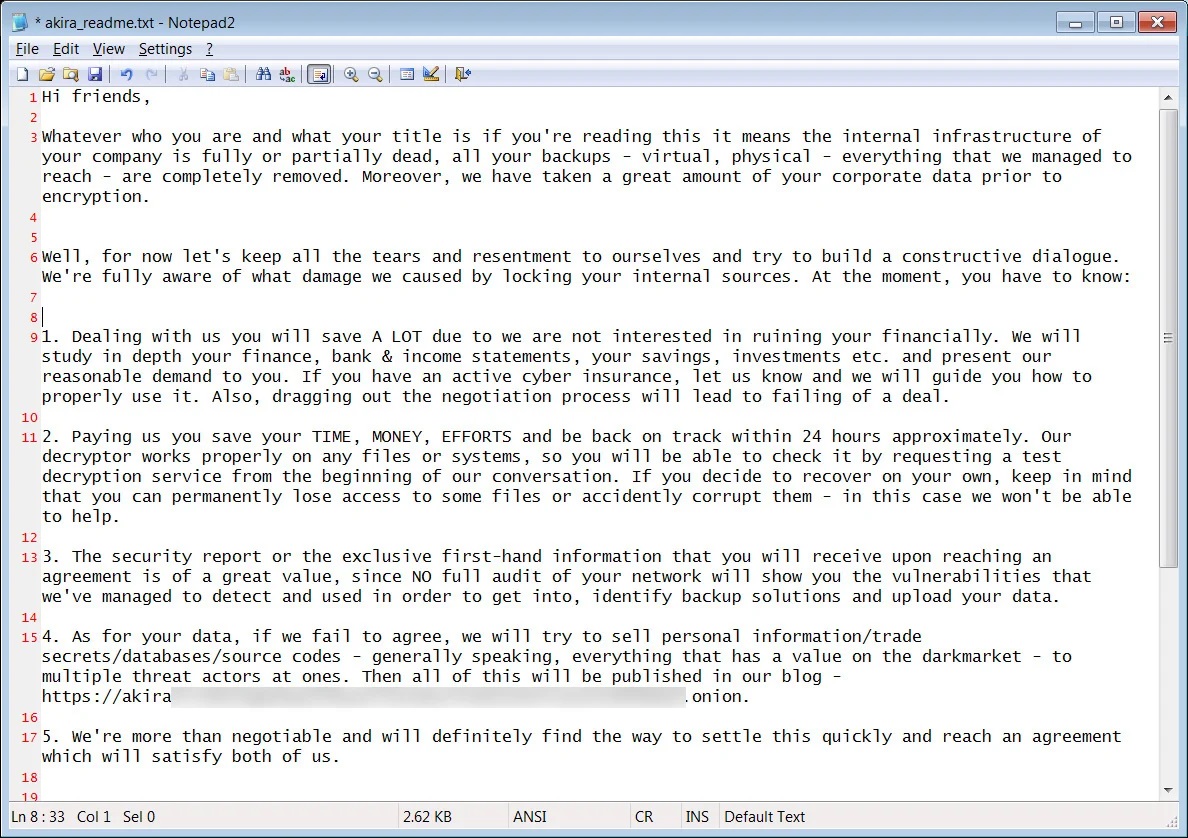 Akira ransom note
Akira ransom note
Source: BleepingComputer
Given the severity of the attacks and the high ransoms being demanded, companies are understandably concerned about the threat posed by Akira. The ransomware is also notable for its wide range of targeted industries, indicating that the attackers are not focused on any one specific sector. The use of the Windows Restart Manager API is another unique feature of Akira that sets it apart from other ransomware operations.
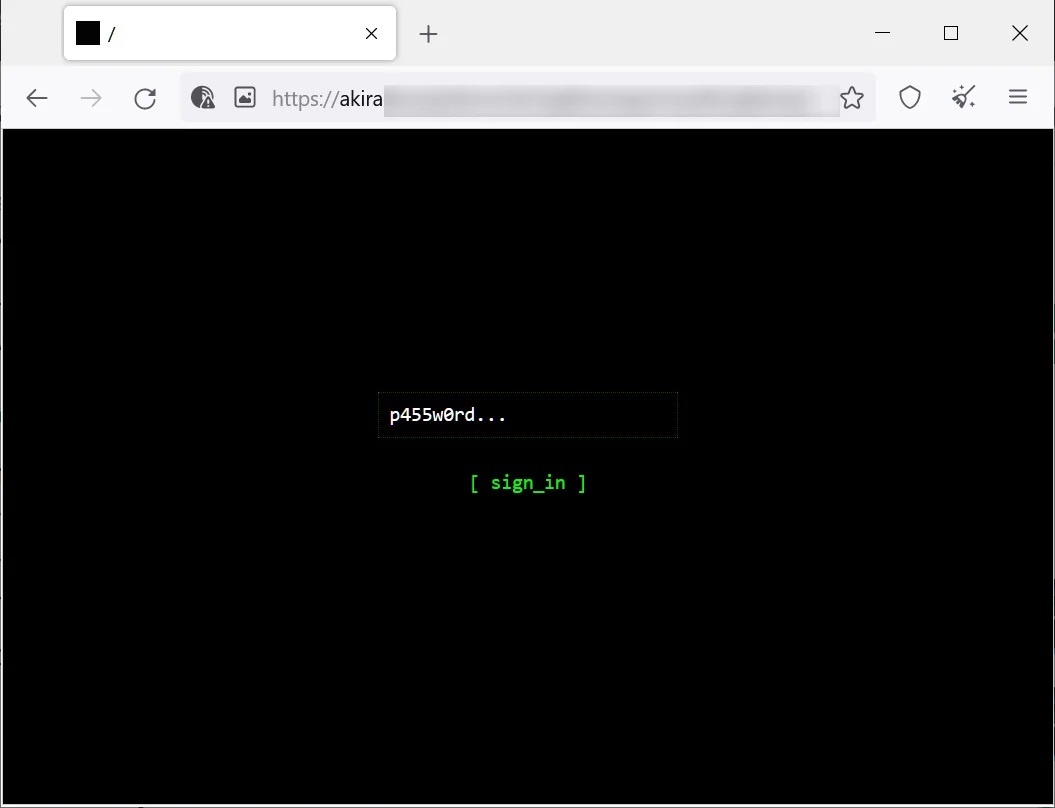 Akira Tor payment site
Akira Tor payment site
Source: BleepingComputer
Data leak site used to extort victims
The gang uses a retro-styled data leak site to extort victims and has already leaked data from four victims. Ransom demands range from $200,000 to millions of dollars, with lower demands for companies who do not need a decryptor. Victims are advised not to pay the ransom until it’s determined if a free decryptor can recover files for free.
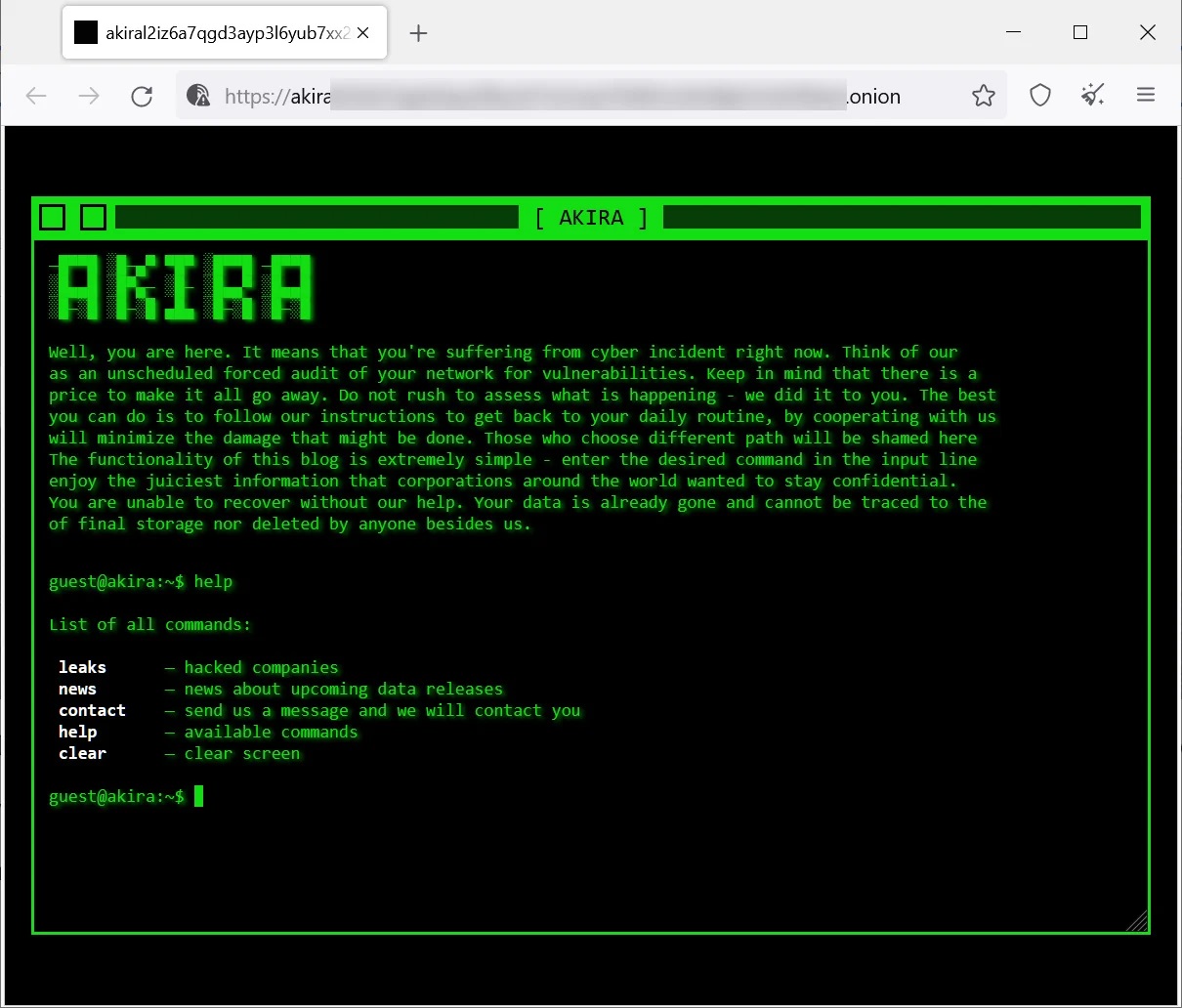 Akira data leak site
Akira data leak site
Source: BleepingComputer
The information is provided solely for general informational and educational purposes and is not intended to be a substitute for professional advice. As a result, before acting on such information, we recommend that you consult with the appropriate professionals.
