- Road No - 3, Banjara Hills, Hyderabad.
- +91-94919 42943
Ransomware Attack Prevention Checklist
Ransomware Attack Prevention Checklist – 2023
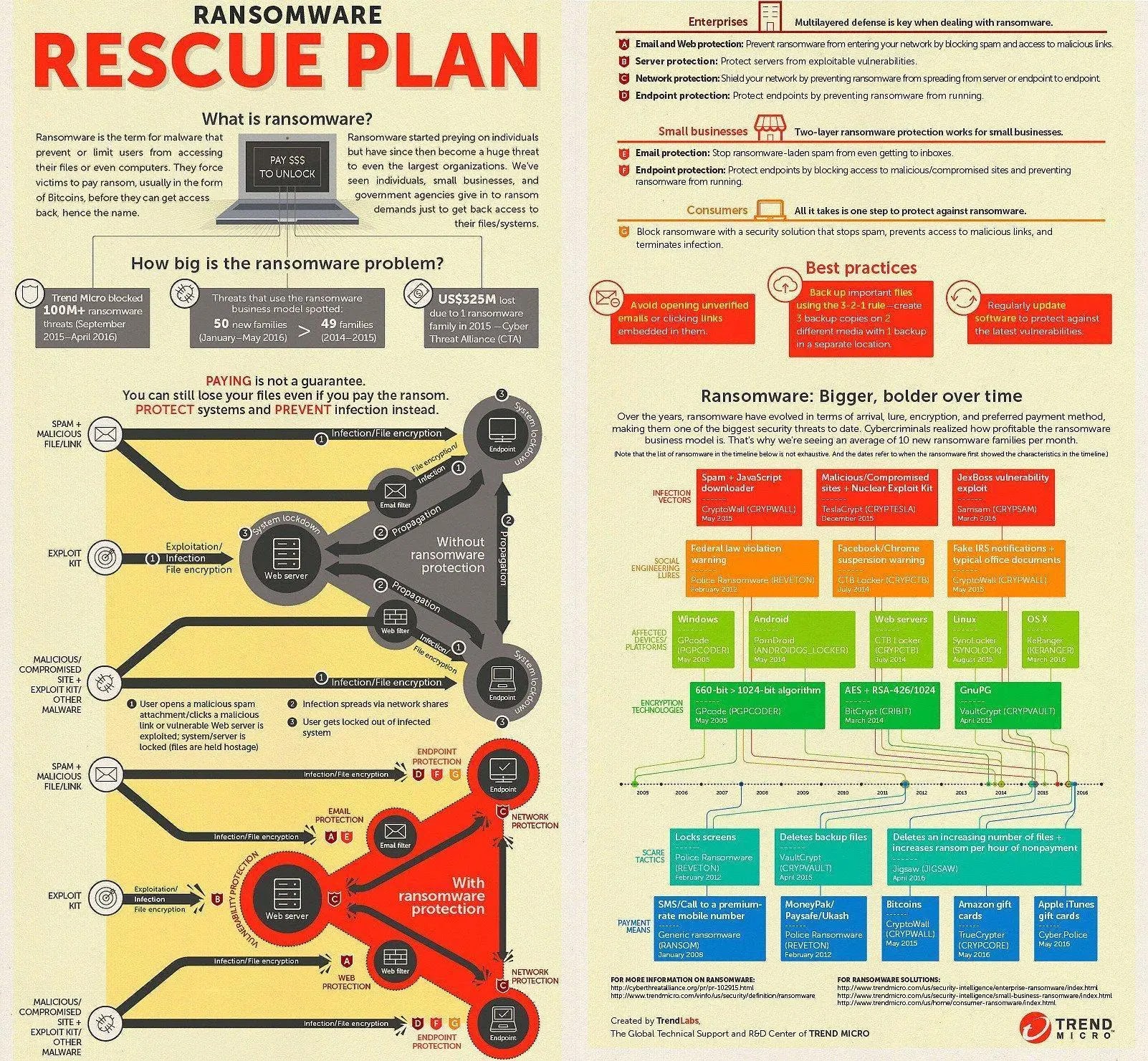
Businesses face significant hazards from ransomware attacks, which are capable of causing severe damage in a brief period.
Over the past few years, numerous well-known companies, including CNA Financial, JBS Foods, and Colonial Pipeline, have fallen victim to such attacks, resulting in disruptions to insurance payments, food supplies, and fuel availability.
These incidents have highlighted the profitability of ransomware deployment for cybercriminals, as organizations have demonstrated a willingness to pay substantial sums, often in the tens of millions, to regain access to their stolen data.
However, repaying the ransom does not ensure the data’s safe return or defend against future hacking attempts.
Implementing a ransomware prevention plan can provide organizations and businesses with the necessary tools to protect your organization and prevent cyber attackers from infiltrating their systems.
By following the ransomware prevention checklist, organizations, and businesses can effectively address this critical threat, avoid costly efforts to restore their environments, and succumb to ransom demands.
What is a Ransomware Attack?
A ransomware attack is a malicious software (malware) designed to prevent users or organizations from accessing their computer files.
The assailants accomplish this by encrypting the files and demanding a ransom for the decryption key.
This puts the affected organizations in a difficult position, as they must decide whether paying the ransom is the quickest and most convenient way to regain access to their files.
Unfortunately, paying the ransom is the only viable option in many cases. However, there are disadvantages to consider when opting for this route, and there is no guarantee that paying the ransom will result in successful file recovery.
Ransomware is a highly noticeable and widespread form of malware.
Recently, it has caused significant disruptions by incapacitating hospitals, paralyzing local governments, and simultaneously inflicting harm on multiple organizations.
The most effective approach to combat ransomware attacks is to focus on preventing them from occurring in the first place.
Types of Ransomware Attacks
Cybercriminals employ several types of ransomware attacks to target individuals and organizations. Here are some common types:
- Encrypting Ransomware: This is the most prevalent type of ransomware. It encrypts files and locks them behind a strong encryption algorithm, rendering them inaccessible to the victim. The attacker’s appetite is a ransom for the decryption key to decrypt the files.
- Locker Ransomware: This ransomware locks the victim out of their entire device, such as a computer or smartphone, rather than encrypting specific files. It displays a full-screen message claiming that illegal activities have been detected and a fine or ransom must be paid to regain access.
- Scareware:Scareware is a form of ransomware that deceives victims by displaying alarming pop-up messages or fake security alerts. These messages claim that the victim’s computer is infected with malware and demands payment for fake antivirus software or system cleanup.
- Mobile Ransomware: As the name suggests, ransomware targets mobile devices like smartphones and tablets. It may lock the device or encrypt files, demanding a ransom for their release. Mobile ransomware can also exploit vulnerabilities in mobile applications or operating systems.
- Ransomware-as-a-Service (RaaS): Ransomware-as-a-Service is a business model where cybercriminals develop and distribute ransomware to other attackers, who then carry out the actual attacks. The developers earn a percentage of the ransom payments made by the victims.
- DDoS Ransomware: Distributed Denial of Service (DDoS) ransomware aims to overwhelm a target’s network or website with a flood of traffic, rendering it inaccessible to legitimate users. Attackers demand a ransom to stop the DDoS attack and restore normal operations.
- Doxware: Also known as leakware or extortionware, doxware threatens to publish or leak sensitive information, such as personal or confidential data unless a ransom is paid. It combines data theft with the threat of public exposure to extort victims.
Most Dangerous Ransomware Groups
It’s important to note that the threat landscape evolves rapidly, and new groups may have emerged since then. Here are some of the most dangerous ransomware groups known at that time:
- REvil (aka Sodinokibi): REvil is a well-known ransomware-as-a-service (RaaS) group that has targeted numerous organizations worldwide. They are known for their high ransom demands and for leaking stolen data if victims refuse to pay. In July 2021, the group temporarily disappeared from the internet after conducting a widespread attack campaign.
- DarkSide: DarkSide gained significant attention in 2021 due to its involvement in the Colonial Pipeline ransomware attack. This group operates as a RaaS and is known for its professionalism, sophisticated techniques, and large ransom demands. After the Colonial Pipeline incident, DarkSide announced that they were disbanding, but it’s not uncommon for such groups to re-emerge under different names.
- Conti: Conti is another RaaS group that emerged in 2020 and quickly gained notoriety. They have targeted organizations across various sectors, including healthcare, education, and government. Conti is known for its targeted approach and extensive data theft before encrypting files.
- Ryuk: Ryuk is an advanced ransomware strain used by multiple threat actors. The group behind Ryuk is believed to have ties to the TrickBot botnet and has conducted numerous high-profile attacks, targeting organizations and demanding large ransom payments.
- Maze: Maze ransomware was active until November 2020, when the group announced its retirement. They gained attention for their “double extortion” tactic, where they encrypted files and exfiltrated sensitive data to pressure victims into paying the ransom.
It’s important to note that the landscape of ransomware groups is dynamic, and new groups can emerge while existing ones may change their tactics or disband.
Organizations must stay updated on the latest threats, maintain robust security measures, regularly patch and update systems, and educate employees about security best practices to mitigate the risk of ransomware attacks.
Top Ransomware Attack Prevention Checklist
Here is a top ransomware attack prevention checklist to help protect your organization:
- Regularly Update Software: Keeping your software up to date is crucial in preventing ransomware attacks. Cybercriminals frequently exploit software vulnerabilities to obtain unauthorized access. Regularly updating your operating system, applications, and security software ensures you have the latest security patches installed, closing any known security vulnerabilities.
- Employee Traininge: Educating your employees about the risks associated with ransomware is essential. Conduct regular training sessions to raise awareness about phishing emails, malicious attachments, suspicious links, and social engineering techniques used by attackers. Teach them how to identify and report potential threats and encourage a culture of cybersecurity awareness throughout the organization.
- Use Strong Passwords and Multi-Factor Authentication: Weak passwords are easy targets for attackers. Encourage employees to construct passwords of letters, numbers, and special characters. Implementing passwordless authentication adds an extra layer of protection by requiring users to provide additional verification, such as a unique code sent to their mobile device and their password.
- Backup Data Regularly: Regularly backing up your critical data is crucial in mitigating the impact of a ransomware attack. Ensure that frequent backups are carried out and stored in a secure location, either on-premises or in the cloud. Test the restoration process periodically to verify that your backups are viable and can be restored.
- Implement Robust Endpoint Protection: Install and regularly update reliable antivirus and anti-malware software on all endpoints, including laptops, desktops, and mobile devices. This software can detect and block known ransomware threats, preventing them from infecting your systems.
- Enable Firewalls and Intrusion Detection Systems: Firewalls segregate your internal network from external threats. Enable firewalls on all network devices to monitor and control incoming and outgoing traffic. Intrusion detection systems can alert you to any suspicious activities or attempted unauthorized access, allowing for immediate action to be taken.
- Segment Your Network: Divide your network into separate segments, also known as network segmentation, to limit the lateral movement of attackers. Compartmentalizing your network prevents an attacker from easily gaining control over the entire infrastructure if one segment is compromised.
- Restrict User Privileges: Grant employees access privileges based on their job requirements. Limit administrative rights to only those who truly need them. Minimizing the number of users with elevated privileges reduces the risk of a compromised account leading to widespread damage or data loss.
- Conduct Regular Security Audits: Regularly assess and audit your systems and networks for vulnerabilities. Identify and address any security weaknesses or misconfigurations that attackers could potentially exploit. Penetration testing and vulnerability assessments can help identify and fix these issues before they are exploited.
- Develop an Incident Response Plan: Create a comprehensive incident response plan outlining the steps to be taken during a ransomware assault. This plan should include procedures for isolating infected systems, notifying appropriate personnel, engaging with law enforcement if necessary, and restoring systems from backups. Review and exercise the incident response plan frequently to ensure its effectiveness.
Ransomware Attack Preventions Tools And Software
Preventing ransomware attacks requires a multi-layered approach that combines various tools, software, and best practices. Here are some preventive measures and security solutions that can help mitigate the risk of ransomware attacks:
- Antivirus and Anti-malware Software: Install and regularly update reputable antivirus and anti-malware software on all systems. These solutions can help detect and block known malware strains, including ransomware.
- Endpoint Protection: Deploy endpoint protection solutions that provide advanced threat detection and behavior-based analysis to identify and block ransomware attacks. These solutions can monitor and protect endpoints like desktops, laptops, and mobile devices.
- Firewalls: Implement firewalls to control and monitor incoming and outgoing network traffic. Firewalls can help block malicious connections and prevent unauthorized access to your network, reducing the risk of ransomware infections.
- Email and Web Filtering: Utilize email and web filtering solutions to block phishing emails, malicious attachments, and access to compromised or malicious websites. These filters can help prevent users from inadvertently downloading ransomware or clicking on malicious links.
- Patch Management: Regularly apply security patches and updates for operating systems, software applications, and firmware to address known vulnerabilities. Vulnerabilities can be exploited by ransomware to gain unauthorized access to systems, so keeping systems up to date is crucial.
- Backup and Disaster Recovery: Implement regular and automated backups of critical data to offline or cloud storage. Ensure that backups are stored
Ransomware Preventions Solutions
Several software companies specialize in providing solutions specifically designed to prevent and mitigate ransomware attacks. Here are some notable examples:
- CrowdStrike:CrowdStrike offers an endpoint protection platform called Falcon, which provides real-time threat intelligence, behavioral analysis, and machine learning to detect and block ransomware attacks.
- Sophos:Sophos provides a range of security solutions, including Intercept X, which offers advanced endpoint protection with anti-ransomware features, exploit prevention, and deep learning technology to detect and stop ransomware attacks.
- McAfee:McAfee offers a comprehensive suite of security products, including endpoint protection solutions with ransomware protection features. Their solutions utilize machine learning and behavior-based analysis to detect and block ransomware attacks.
- Symantec (now part of Broadcom): Symantec offers a range of security products, including their Endpoint Protection solution, which includes advanced threat prevention capabilities to defend against ransomware attacks.
- Trend Micro: Trend Micro provides various security solutions, including their Apex One endpoint protection platform that incorporates advanced threat detection and response capabilities to defend against ransomware attacks.
- Bitdefender: Bitdefender offers a range of security products, including their GravityZone suite, which provides endpoint protection with anti-ransomware features, as well as advanced threat intelligence and machine learning algorithms.
- Cisco: Cisco offers a range of security solutions, including endpoint protection, firewalls, email and web filtering, and threat intelligence. Their solutions are designed to provide advanced threat detection and prevention, including ransomware attacks.
- Kaspersky: Kaspersky provides antivirus and anti-malware software, endpoint protection, and threat intelligence solutions. Their solutions use advanced behavior-based analysis and machine learning to detect and prevent ransomware attacks.
Disclaimer: The information is provided solely for general informational and educational purposes and is not intended to be a substitute for professional advice. As a result, before acting on such information, we recommend that you consult with the appropriate professionals.

